
Was ist Firewall-as-a-Service (FWaaS)?
- Cloud networking
- 1. September 2022
Sie würden nicht einfach jeden in Ihr Haus lassen, und mit Ihrem Netzwerk sollte es nicht anders sein. Hier erfahren Sie, wie Firewall as a Service (FWaaS) als Sicherheitsbeauftragter Ihrer Cloud-Infrastruktur fungiert und für besseren Datenschutz sorgt.
Da Cyberangriffe immer häufiger und ausgeklügelter werden, ist es wichtiger denn je, die Sicherheit Ihres Netzwerks zu überdenken. Während mehr Unternehmen ihr Cloud-Potenzial ausschöpfen und auf “as-a-service”-Lösungen wie Network as a Service (NaaS) und Software as a Service (SaaS) setzen, um die vielen Vorteile der Cloud-Technologie zu nutzen, gibt es eine weitere Cloud-Lösung, die Ihnen helfen könnte, Ihr Netzwerk zu schützen: Infrastructure as a Service (IaaS) oder genauer gesagt Firewall as a Service (FWaaS).
“As a Service”-Modelle beziehen sich einfach darauf, wenn IT-Dienstleistungen auf Abruf bereitgestellt werden, entweder remote über die Cloud eines Network as a Service Providers (NaaS). Aufgrund ihrer cloud-nativen Natur erfordern diese Dienste wenig bis gar keine Investitionsausgaben und können anpassungsfähig skaliert werden, um den sich ändernden Bedürfnissen Ihres Unternehmens gerecht zu werden. Als solche unterscheidet sich FWaaS von traditionellen Firewalls, da es dem Kunden über die Cloud oder einen NaaS-Anbieter bereitgestellt wird, ohne die Notwendigkeit der Installation und Wartung von Hardware einer lokalen Infrastruktur.
Eine Netzwerk-Firewall könnte mit einem Sicherheitsbeauftragten eines Gebäudes verglichen werden, der anhält, um die Identität derjenigen zu überprüfen, die versuchen einzutreten, und denen den Zutritt verweigert, die keine Erlaubnis haben. Ihre Netzwerk-Firewall übernimmt eine ähnliche Rolle – indem sie den Verkehr, der einzutreten versucht, beurteilt, kann Ihr Netzwerk vor unbekannten und unerwünschten Bedrohungen geschützt werden.
Bevor Unternehmen globalisierter und mobiler wurden, waren traditionelle, auf Büros beschränkte Firewalls ausreichend, und IT-Abteilungen mussten eine Firewall nicht über ihren ursprünglichen Installationsort hinaus erweitern. Aber heute sind die Grenzen von Firewalls stark erweitert, mit zahlreichen Endpunkten, um den Anforderungen globaler Arbeitskräfte gerecht zu werden.
Wie funktioniert Firewall as a Service?
Positioniert zwischen Ihrem Unternehmensnetzwerk und dem öffentlichen Internet arbeitet FWaaS daran, Ihre Architektur vor Cyberangriffen durch mehrere Filter- und Sicherheitsmaßnahmen vor eingehendne Bedrohungen zu schützen. Solche Maßnahmen umfassen automatisierte Reaktionen bei Bedrohungserkennung, vollständige Ereignisprotokollierung, Intrusion Prevention System (IPS) und Domain Name System (DNS)-Sicherheit.
Wenn der Verkehr versucht, in Ihr Netzwerk einzutreten, inspiziert die FWaaS-Lösung ihn zuerst, um jegliche Art von Bedrohungen zu erkennen. Durch die Analyse der Informationen aus jedem Datenpaket – wie zum Beispiel, woher es kam oder Anzeichen von bösartigem Inhalt – kann es dann entsprechend akzeptiert oder abgelehnt und daran gehindert werden, in Ihr Netzwerk einzudringen.
Darüber hinaus bieten Next Generation Firewalls (NGFW) weitaus größere Fähigkeiten im Vergleich zu traditionellen, älteren Firewalls mit Bewusstsein und Kontrolle über Anwendungen, fortschrittlicher Malware-Erkennung über Sandboxing und tief integrierter IPS.
IT-Abteilungen können ihre FWaaS an ihre spezifischen Bedürfnisse anpassen, einschließlich der Frage, welches Personal auf welche Daten zugreifen kann, indem bestimmte Logins, Websites, IP-Adressen und mehr herausgefiltert werden. Dies dient dazu, Unternehmen sowohl vor internen als auch externen Bedrohungen zu schützen.
Warum benötigen Organisationen FWaaS?
Die Entscheidung für FWaaS gegenüber traditionellen Hardware-Firewalls vor Ort oder alternativen Netzwerkschutzmaßnahmen kann aus vielen Gründen vorteilhaft sein, einschließlich:
- Sichtbarkeit – FWaaS bietet On-Demand-Sichtbarkeit und Kontrolle über Ihre Sicherheitsmaßnahmen, Benutzer, Anwendungen und Standorte. Durch die detaillierte Protokollierung jeder Sitzung und die Nutzung von Deep Learning zur Erkennung von Angriffsmustern kann Ihr Unternehmen bessere Einblicke in Netzwerkschwachstellen gewinnen.
- Zero Trust Bereitschaft – Wenn es um Cloud-Sicherheit geht, gibt es keine bessere Option als ein Zero Trust Framework. Durch die Nutzung von FWaaS als Teil von Zero Trust können Sie Sicherheitsrichtlinien zu Benutzern an ihren Endpunkten in Übereinstimmung mit einem Secure Access Service Edge (SASE)-Framework bringen – ein Muss im Zeitalter der Remote-Arbeit. Außerdem reduziert Zero Trust die Latenz, indem es direkt über das Internet mit Apps verbindet.
- Echtzeit globale Rechenkapazität und schnelle Bereitstellungszeit – Aufgrund von Lieferkettenproblemen warten viele IT-Abteilungen außergewöhnlich lange auf Hardware-Firewalls. Aber FWaaS kann diese Fähigkeit in Echtzeit liefern.
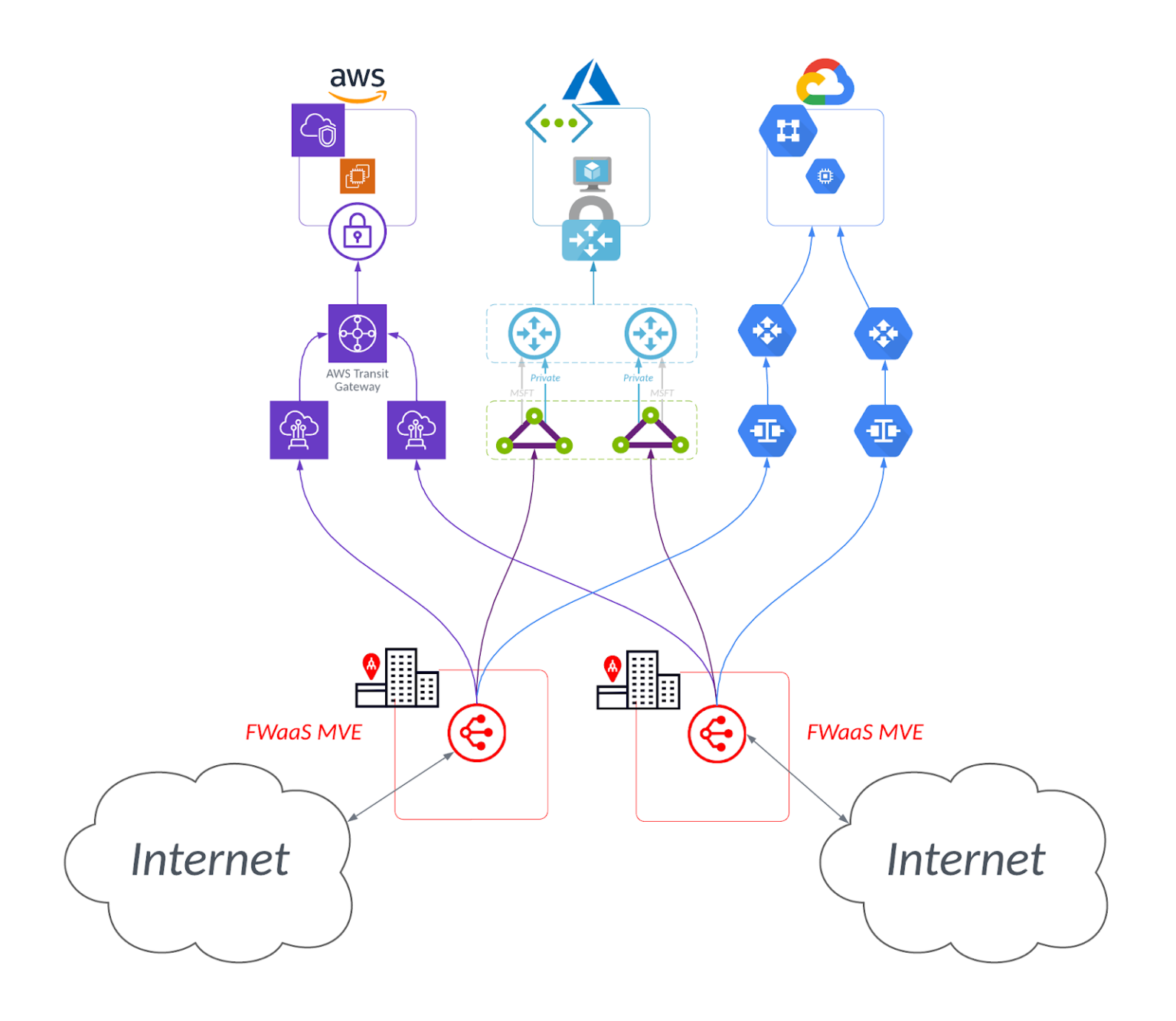
- Geografische, Zugriffs- und technologische Redundanz – Wenn es als Teil einer Network Function Virtualization (NFV)-Lösung für SD-WAN, wie MVE, verwendet wird, können Sie FWaaS in anderen Rechenzentren für Redundanz und Vielfalt bereitstellen. Sie können auch auf Ihr Netzwerk zugreifen, indem Sie IPSec über das Internet verwenden, als Backup für Ihre primäre Glasfaserroute.
- Benutzerdefinierte Konfigurationen – Mit dem richtigen Anbieter können Sie FWaaS als maßgeschneiderten Router verwenden und ihn so konfigurieren, dass Sie noch mehr Vorteile für Ihr Netzwerk erzielen – zum Beispiel die Überwindung von AWS Transit Gateway-Limits.
FWaaS als Teil Ihrer SASE-Infrastruktur
Eine FWaaS-Lösung kann auch Teil Ihrer Secure Access Service Edge (SASE)-Infrastruktur sein. SASE bezeichnet „ein Framework, das die besten Elemente von softwaredefiniertem Networking und SD-WAN mit modernisierter Edge-Sicherheit vereint“. Es umfasst Komponenten wie softwaredefinierte Wide Area Networks (SD-WAN), Secure Web Gateway (SWG) und Zero Trust Network Access (ZTNA), um ein leistungsstarkes, sicheres Netzwerk an der Edge für Ihr Unternehmen zu schaffen.
Innerhalb eines SASE-Frameworks arbeitet FWaaS mit anderen Sicherheitslösungen zusammen, um die Netzwerkgrenzen vor Cyberangriffen zu schützen. Kunden können sich dabei auf einen einzigen Anbieter verlassen, anstatt mehrere Drittanbieter integrieren zu müssen. Das Ergebnis ist eine transformierte Netzwerkarchitektur, die dynamisch, flexibel und sicher ist und die Leistung liefert, die für heutige Anwendungen und Ressourcen in öffentlichen, privaten und hybriden Clouds erforderlich ist.
Anwendungsfälle
Die Vorteile der Integration von FWaaS in Cloud-Infrastrukturen sind klar, aber für wen ist die Lösung am besten geeignet? Es gibt verschiedene Anwendungsfälle für die Implementierung von FWaaS, darunter:
- Sicheres Bereitstellen aller benötigten Anwendungen auf Unternehmensnetzwerken
FWaaS hilft, Angriffe durch Unternehmensanwendungen zu erkennen. Es ermöglicht die Durchsetzung spezifischer Kontrollmaßnahmen für die Funktionalität von Anwendungen, die Überwachung von Anwendungsdaten und -inhalten und vieles mehr. - Schutz vor bekannten und unbekannten Bedrohungen, unabhängig von den verwendeten Anwendungen
FWaaS ermöglicht äußerst granulare Kontrollen für Netzwerkanwendungen. Mit Funktionen wie Deep Packet Inspection und zustandsbasierter Inspektion von Anwendungen in Echtzeit bietet eine Next Generation Firewall (NGFW) starken Schutz vor bekannten und unbekannten Bedrohungen für Ihre Webanwendungen. - Bereitstellung von Notfallzugriff und langfristiger Redundanz
Richten Sie FWaaS als temporäre Zugriffsmethode in Regionen ein, die mit Last-Mile-Netzwerkproblemen oder MPLS-Ausfällen zu kämpfen haben. Der redundante Pfad, den FWaaS bietet, ist auch eine gute Backup-Option für langfristige Redundanz. - Absicherung von VPN-Gateways
Mit FWaaS als Sicherheitsschicht für VPN-Gateways erhalten Sie einen zentralen Netzwerk-Einstiegspunkt für sichere und leistungsfähige Verbindungen. Außerdem können Sie ein einzelnes Gateway schnell und einfach gestalten, was Zeit, Kosten und Komplexität reduziert, die mit der Verwaltung mehrerer Tunnel einhergehen. FWaaS ermöglicht es zudem, SASE-Endpunkte bereitzustellen, um strenge, richtlinienbasierte Sicherheitsdienste für Endbenutzer zu gewährleisten. - Überwindung von Cloud-basierten Limitationen
Durch maßgeschneiderte Firewall-Konfigurationen können Sie bestimmte Zugriffsgrenzen umgehen, die von Cloud Service Providern (CSPs) auferlegt werden, wie z. B. die Limits eines AWS Transit Gateways.
FWaaS nicht zu haben, ist „wie keinen Virenschutz auf Ihrem Computer zu haben“. Daher wird der Einsatz für jedes Unternehmen empfohlen, das regelmäßig mit der Cloud interagiert oder geschäftskritische oder sensible Daten verarbeitet. FWaaS eignet sich besonders gut für große Organisationen, die viele remote arbeitende Mitarbeiter haben, die Anwendungen auf mehreren Geräten nutzen.
Wie Megaport helfen kann
Mit Megaport Virtual Edge (MVE) können Kunden FWaaS mit einer Pay-as-you-go-Struktur, die flexibel und skalierbar ist.
Über MVE bereitgestellte FWaaS bietet die Vorteile einer Next Generation Firewall (NGFW). Diese geht über die traditionellen Fähigkeiten einer Firewall hinaus, indem sie nicht nur den ein- und ausgehenden Datenverkehr überwacht, sondern auch eine tiefere Anpassung und maschinelles Lernen für die Erkennung von Bedrohungen und Mustern ermöglicht.
Firewall as a Service kann eine wertvolle und notwendige Ebene für die Infrastruktur Ihres Unternehmensnetzwerks darstellen. Mit On-Demand-Funktionen haben Nutzer die volle Kontrolle über ihr Netzwerk. Als eine Art Wachhund gegen eingehende Bedrohungen sorgt FWaaS für zusätzliche Sicherheit, damit Ihr Team beruhigt arbeiten kann, in dem Wissen, dass Ihr Netzwerk durchgehend geschützt ist.
Entdecken Sie, wie FWaaS über MVE Ihr Unternehmen unterstützen kann – buchen Sie noch heute eine Demo.


