What is Firewall as a Service (FWaaS)?
- September 1, 2022
You wouldn’t let just anyone enter your home, and your network should be no different. Here’s how Firewall as a Service (FWaaS) acts as your cloud infrastructure’s own security guard for better data protection.
With cyberattacks becoming more frequent and advanced than ever before, there’s never been a more critical time to reconsider your network security. As more businesses realize their cloud potential and turn to as-a-service solutions – such as Network as a Service (NaaS) and Software as a Service (SaaS) – to take advantage of cloud technology’s many advantages, there’s another cloud solution that could help you protect your network: Infrastructure as a Service (IaaS) or more specifically Firewall as a Service, or FWaaS.
“As a service” models simply refer to when IT services are delivered on-demand, either remotely through the cloud of a Network as a Service Provider (NaaS). Due to their cloud-native nature, these services require little to no capital expenditure, and can be adaptable to scale over time to suit your businesses’ changing needs. As such, FWaaS differs from traditional firewalls as it’s delivered to the customer through the cloud or a NaaS provider, without the need for installation and hardware maintenance of any on-premises infrastructure.
A network firewall could be compared to a building’s security guard, stopping to verify the identity of those who attempt to enter and refusing entry to those who don’t have permission. Your network firewall takes on a similar role – by assessing traffic attempting to enter, your network can be protected from unknown and unwanted threats.
Before companies became more globalized and remote, traditional firewalls localized to offices were sufficient, and IT departments had no need to extend a firewall beyond its original installation site. But today, the borders of firewalls are heavily expanded, with endpoints everywhere to meet demands of global workforces and devices without clearly defined network borders.
How does Firewall as a Service work?
Positioned between your enterprise network and the public internet, FWaaS works to protect your architecture from cyberattacks through multiple filtering and security measures that prevent incoming threats from penetrating your network. Such measures include automated responses upon threat detection, full event logging, intrusion prevention system (IPS), and Domain Name System (DNS) security.
As traffic attempts to enter your network, the FWaaS solution first inspects it to detect any kind of threats. By analyzing the information from each data packet—such as where it came from, or any signs of malicious content—it can then subsequently accept it, or reject and deter it from entering your network.
In addition, Next Generation Firewalls (NGFW) provides much greater capabilities compared to traditional, older firewalls with awareness and control over applications, advanced malware detection via sandboxing, and deep integrated IPS.
IT departments can customize their FWaaS to suit their specific needs, including which staff can access which data by filtering out certain logins, websites, IP addresses, and more. This is to safeguard enterprises from both internal and external threats.
Why organizations need FWaaS
Opting for FWaaS over traditional on-site hardware, firewalls, or alternative network protection measures can prove beneficial for many reasons, including:
- Visibility – FWaaS delivers on-demand visibility and control over your security measures, users, applications, and locations. By logging every session in detail and using deep learning to recognize attack patterns, your business can gain better insights into network vulnerabilities.
- Zero trust readiness – when it comes to cloud security, there’s no better option than a zero trust framework . By leveraging FWaaS as a part of zero trust, you’re able to bring security policies to users at their endpoints in line with a secure access service edge (SASE) framework—a must-have in the era of remote work. What’s more, zero trust reduces latency by connecting to apps directly over the internet.
- Real-time global compute capability and quick time to deploy – due to supply chain issues , many IT departments are waiting an extraordinary length of time for hardware firewalls. But FWaaS can deliver this capability in real time.
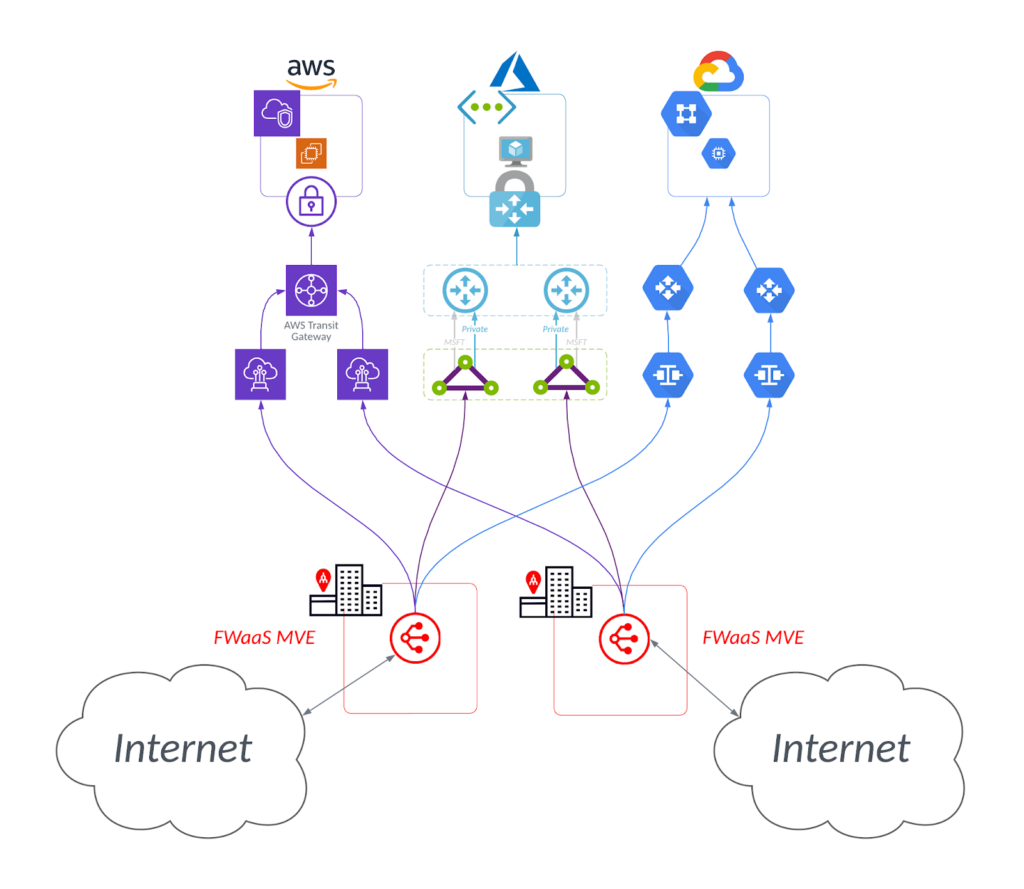
- Geographical, access, and technological redundancy – when used as part of a Network Function Virtualization (NFV) solution for SD-WAN, like MVE , you can provision FWaaS in other data centers for redundancy and diversity. You can also access your network by using IPSec over the internet, as a backup to your primary fiber route.
- Custom configurations - with the right provider, you can use FWaaS as a bespoke router and configure it to get even more benefits for your network – for example, overcoming AWS Transit gateway limits.
FWaaS as part of your SASE
A FWaaS solution can also form part of your Secure Access Service Edge (SASE) infrastructure. SASE refers to “a framework for converging the best elements of software-defined networking and SD-WAN with modernized edge security” , and encompasses elements such as software-defined wide area networking (SD-WAN), Secure Web Gateway (SWG) , and Zero Trust Network Access (ZTNA) to create a supercharged, secure network at the edge for your enterprise.
Within a SASE framework, FWaaS works alongside other security products to defend the network perimeter from cyberattacks, with customers able to rely on a single vendor rather than multiple third-party vendors. The end result is a transformed network architecture that is dynamic, flexible, and secure, and can provide the performance needed for today’s 24/7 applications and resources hosted across public, private, and hybrid clouds.
Use cases
The benefits of integrating FWaaS into cloud infrastructures are clear, but who does the solution suit best? There are a number of use cases for implementing FWaaS. These include:
- Safely enabling all required applications on enterprise networks – help detect attacks through enterprise applications. Enforce application functionality specific controls, monitor application data and content, and more.
- Protection against known and unknown threats, irrespective of the applications used to transport the threats – FWaaS allows very granular controls for network applications. With its deep packet inspection capabilities and state-full inspection of applications in real-time, Next Generation Firewall (NGFW) provides robust defense against known and unknown threats against your web applications.
- Provide emergency access and long-term redundancy – set up FWaaS as a temporary access method for regions that are experiencing last-mile network issues or core MPLS failures. The redundant path that FWaaS provides is also a good backup option for long-term redundancy.
- Secure VPN gateways – by using FWaaS as a security layer for any VPN gateways you create, you’ll get a central network entry point for more secure and performant network connections – plus, you can quickly and easily architect a single gateway, saving time, costs, effort, and confusion that can arise from managing several tunnels. In addition, FWaaS enables customers to also deliver SASE end points to provide strict policy-based security services for end users.
- Overcome cloud-enforced limits or quotas – by providing bespoke configurations on the firewalls, you can bypass certain access limits placed by CSPs (like those AWS transit gateway limits we mentioned earlier).
Not having FWaaS is “like not having an antivirus on your computer” , so adopting it is advisable for any enterprise who interacts with the cloud daily, or deals with mission-critical or private-natured data. FWaaS best suits large organizations that have many remote employees accessing applications across multiple devices.
How Megaport can help
Through Megaport Virtual Edge (MVE) , customers can enable FWaaS for their enterprise network in more than 20 metros with a pay-as-you-go, scalable setup.
With FWaaS delivered via MVE, users can enjoy the benefits of Next Generation Firewall (NGFW), a network security device that goes beyond traditional firewall capabilities to not only inspect ingoing and outgoing traffic on your network, but also allow greater customization and deep learning of data threats and patterns.
Firewall as a Service can prove a valuable and necessary layer to your enterprise network’s infrastructure, giving users full control of their network with features available on-demand. By acting as a protective watchdog against incoming threats, your team can have peace of mind knowing that FWaaS is constantly acting as an additional security layer over your network, protecting it from cyberthreats.
Discover how FWaaS delivered via MVE can help your business – book a demo today.