
Q and A for Q-in-Q part 1
- Tech
- September 13, 2016
In this two part blog series, we will cover some of the basics around double-stacked VLAN tagging, otherwise known as Q-in-Q, or by it’s formal IEEE definition, 802.1ad.
What is VLAN tagging?
There are two types of ports on network switches. Most vendors use terms such as “Trunk Port” and “Access Port” to differentiate them. Access ports define a port where a single VLAN ID is carried whereas Trunk ports carry traffic destined for multiple VLANs. Trunk Ports require a policy to determine which traffic is to be sent within which VLAN identifier. For these purposes, a technical standard defining VLAN tagging 802.1q was developed. These VLAN tags contains information such as VLAN ID and other information that is specified by the 802.1q standard.
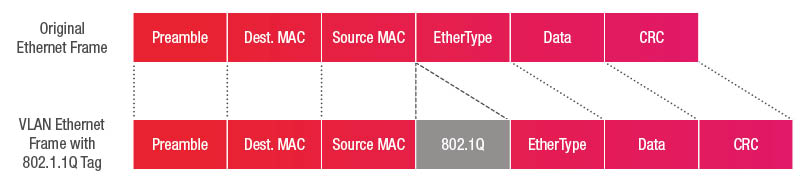
What does the technical outline of 802.1q (single tagged VLAN frames) look like?
An Ethernet frame (a physical layer communications transmission unit) that belongs to a VLAN which is carried through a Trunk Port will have a 802.1q header added. See the following diagram:
What is Q-in-Q?
Q-in-Q (formally defined as 802.1ad) is developed based around 802.1q (VLAN tagging) to provide an additional layer of flexibility when dealing with Layer 2 networking. It was originally designed to allow Network Service Providers (NSPs) flexibility in handling trunk port capability but spanning multiple customer connections that may wish to re-use the same VLAN. Q-in-Q tunnelling allows NSPs to consolidate all VLAN traffic into a single VLAN by adding an additional VLAN tag to already tagged traffic sent to and from customers. The additional tag helps NSPs to identify and separate different customer traffic.
Within an Ethernet Frame, these two tags are often known as “Inner tag” and “Outer tag”. “Inner tags” contain VLAN information that belong to the traffic of the NSP’s customers. The “Outer tags” contains information relating to the NSP’s VLAN networks. Though Q-in-Q/ 802.1ad was designed originally for NSPs to add/remove transparently to a customer (so called ‘pushing’ and ‘popping’ of outer tags) it is routinely utilised to carry a range of VLANs across a single VXC. This would allow for example a partner utilising Megaport to aggregate traffic on behalf of multiple customer networks and carry them transparently as a single VXC between two network locations, even where other customers using the same aggregator may utilise a similar group of VLAN identifiers.
What is a Q-in-Q Frame Build (802.1ad)?
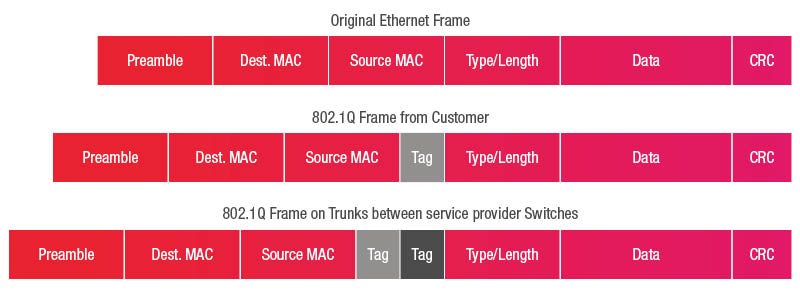
Tag in light grey = Outer Tag
Tag in dark grey = Inner Tag
How can I differentiate the inner tag from the outer tag? Does it matter?
As you can imagine there is a definite need to isolate the double stacked tags. You might have heard the story about the great thing about standards – there’s a few of them so pick the one that suits you best! To differentiate the different tags under the 802.1ad standard the inner commonly uses EtherType 0x8100 and outer 0x88a8 whilst the Cisco definition of Q-in-Q is for both inner and outer EtherTypes to be 0x8100. It is important to note that the Megaport specification of double-tagged frames is for both inner and outer tags to be 0x8100.
This double tagged VLAN concept is also frequently used in direct connectivity to cloud computing resources such as that presented by the Microsoft ExpressRoute product offering. In this specific instance “Inner tags” (or C-TAGs) belong to the Microsoft customer’s multiple VLANs (Azure private, Azure public and Microsoft peering) and “Outer tags” (Service Provider tags, or S-TAGs) belong to the Megaport customer’s A-end VLAN that is requested to be set on their Megaport.
In part two of this series we will explore further the use of this concept for Microsoft ExpressRoute and how to configure redundant connectivity to Azure primary and secondary router presentations. Click here to read part 2 .


